Tag: python
-
Robot Odyssey Chip Disassembler
I’ve been spending more time hacking on Robot Odyssesy lately. Most of it has had a specific purpose… I’ll write a separate blog post on that project once it’s a bit more fully baked. In the mean time, the reverse engineering has had some useful side-effects. Chip Simulation If you haven’t heard of Robot Odyssey,…
-
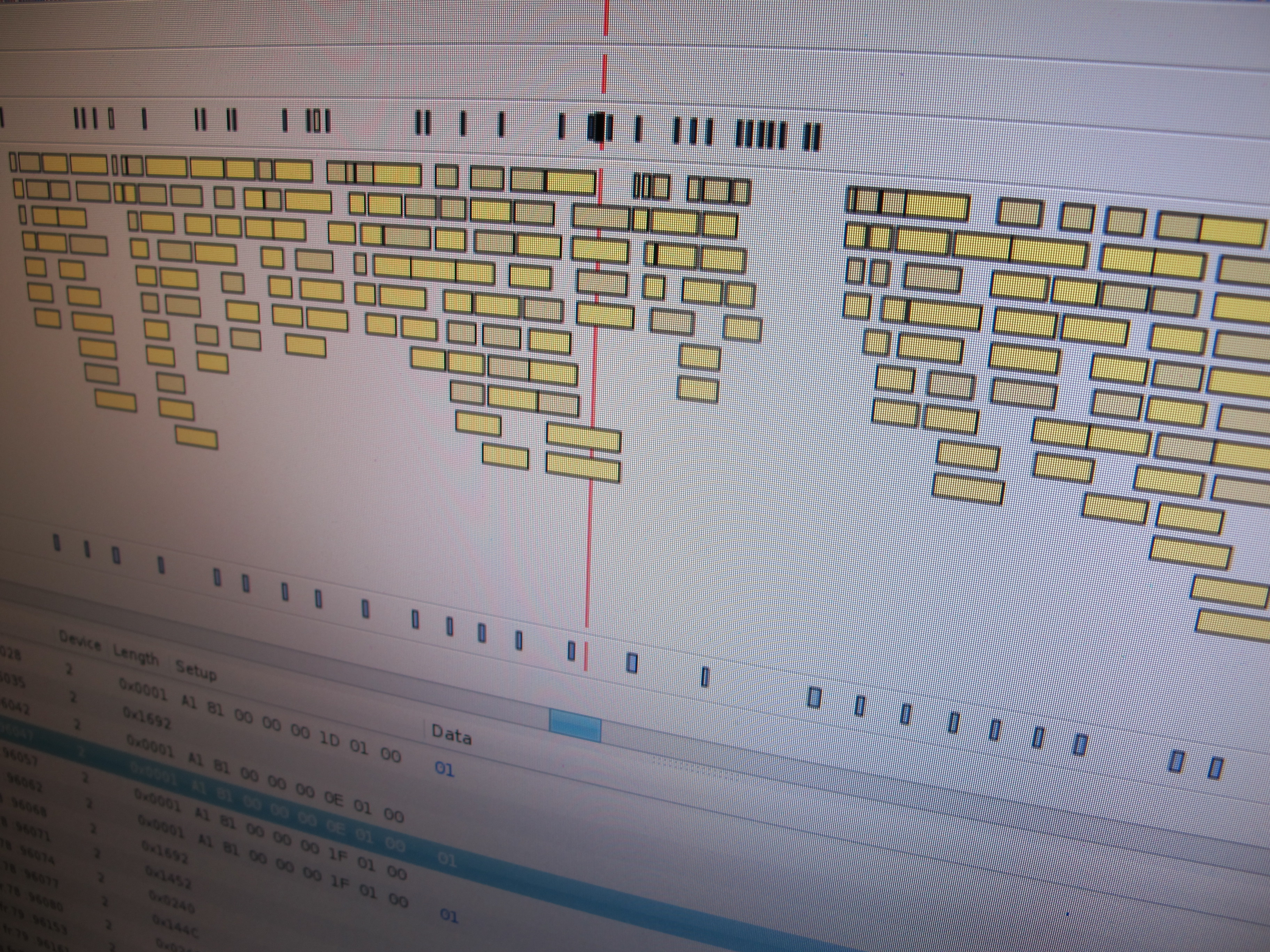
Virtual USB Analyzer
From late 2005 to early 2007, I worked on the USB virtualization stack at VMware. We ran into all sorts of gnarly bugs, many of which were very hard to reproduce or which required access to esoteric or expensive hardware. To help with debugging problems both internally and with customers in the field, we added…
-

Laser projector update
Looks like my hard disk laser projector made the MAKE blog. Sweet 😉 I’ve been hacking on the software for the projector quite a bit this week- mostly on the code responsible for importing and converting vector graphics data. In a typical laser projector, you have a high-speed DAC connecting a pair of analog servo…
-

Times New Roman at 532 nanometers
After running the ILDA test pattern at only 4K on my hard disk laser scanner, I really wanted to see how well the projector would do with the kinds of “real” vector graphics that I expected to be able to display. Most commercial ILDA frames are way too complicated for it. As I mentioned, the…
-
Mobile map inspiration
So, I’ve been itching to do something really cool with Python on Symbian Series 60. The first thought was a way to upload images directly from the phone to Gallery. Well, it still needs some polishing, but I wrote most of that at the last SVLUG hackfest. Right now it takes a picture with the…
